Secure workloads in OpenShift

In this blog post I will discuss the OpenShift security use cases that Red Hat Advanced Cluster Security for Kubernetes addresses and identify the benefits of taking a Kubernetes-native approach to securing your containerized applications in OpenShift.
Containers and microservices initiated a shift in application infrastructure, and Kubernetes has emerged as one of the most quickly adopted technologies ever, helping companies automate the management of these application building blocks. This massive change in infrastructure has driven a parallel change in security, as new tooling and processes are needed to apply controls to the cloud-native stack.
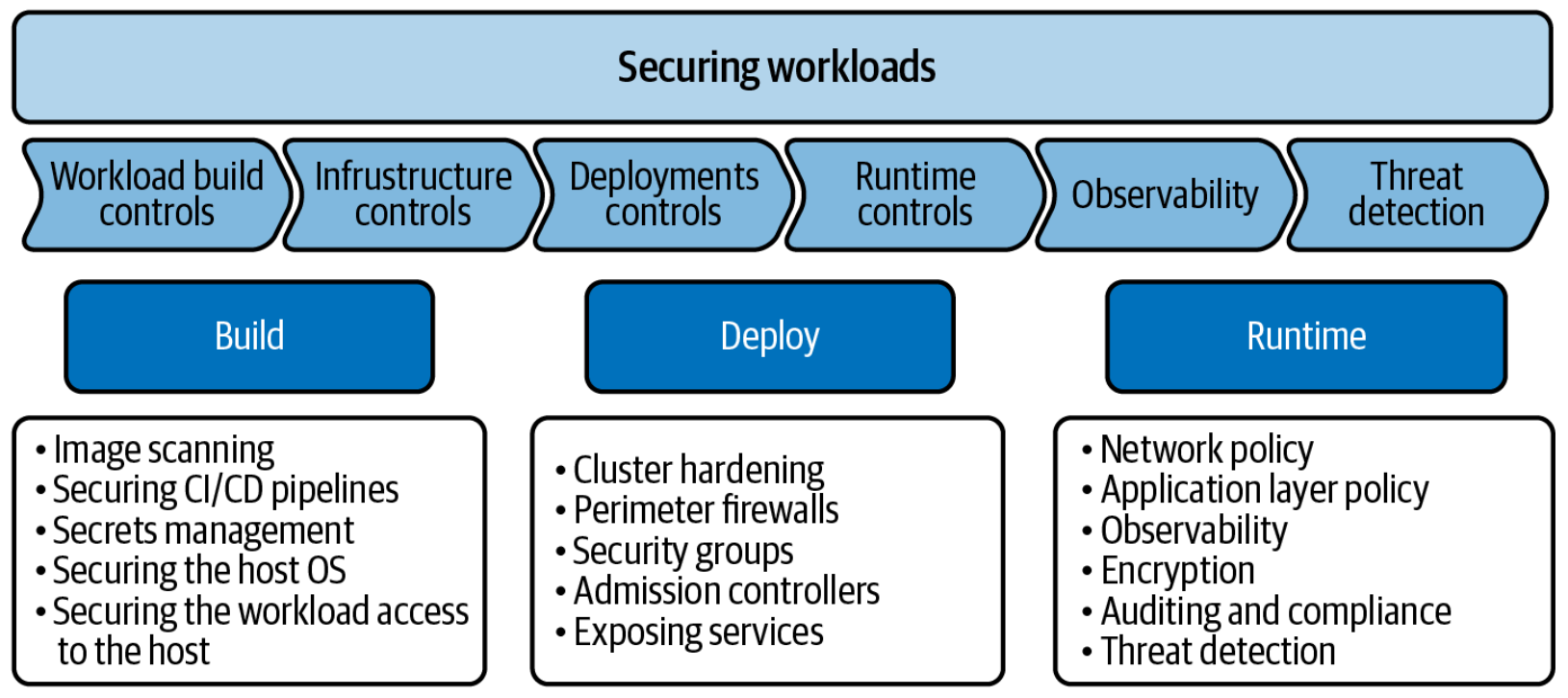
In today’s Kubernetes world, it is no longer adequate to secure just your images and containers. You need a security platform that protects your entire Kubernetes environment across the entire applications lifecycle covering Build, Deploy and Runtime applications lifecycle phases.
Source: https://www.tigera.io/lp/kubernetes-security-and-observability-ebook/
Benefits of Kubernetes-Native Security
Red Hat Advanced Cluster Security for Kubernetes was purpose-built for the modern cloud-native stack. We have built multiple deep integrations with Kubernetes into our platform, making your security as portable, scalable, and resilient as your hybrid cloud infrastructure. This Kubernetes-native approach also delivers the most comprehensive set of container and Kubernetes security capabilities across the full application life cycle.
These advantages, derived from our tight integrations with Kubernetes, enable a better security outcome. While many container security providers highlight a common set of use cases, how you deliver those use cases impacts the result. The following discussion of the top OpenShift security use cases illustrates the advantages of applying a Kubernetes-native architecture.
Visibility
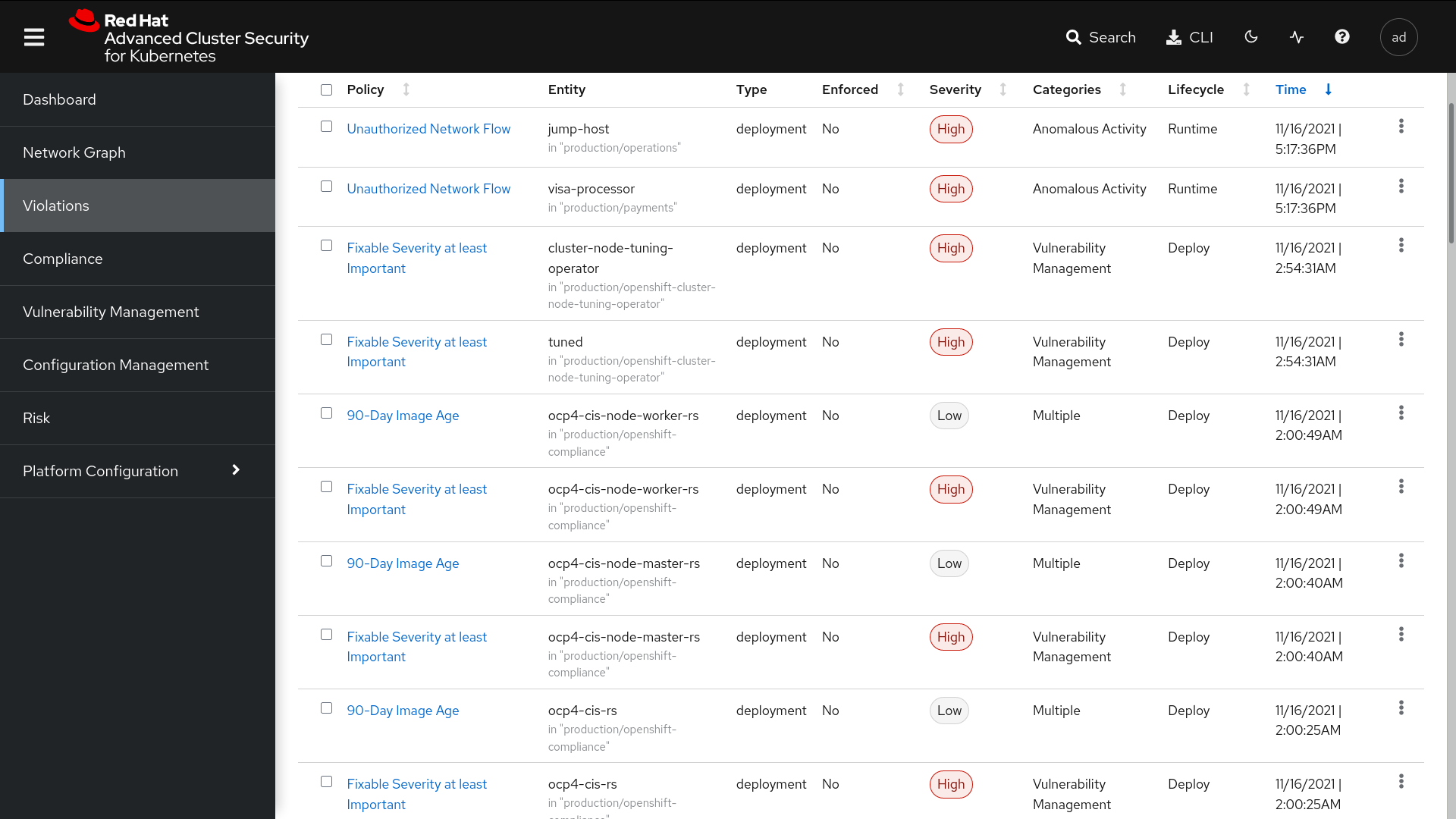
You cannot secure what you cannot see. As a first step, you must gain visibility into your OpenShift environment. You should know what images you are using, understand their provenance, whether they contain any vulnerabilities and their severity level, and that is just the start. You must also know which pods, namespaces, and deployments are running vulnerable containers and their attack surface and potential blast radius in the event of a breach.
Red Hat Advanced Cluster Security for Kubernetes provides visibility into your entire OpenShift environment and accompanying security issues, including the images, containers, and vulnerabilities with CVE and severity scores
This visibility is enhanced with contextual data from Kubernetes, such as allowed network paths, runtime process execution, secrets exposure, and other attributes of the environment.
Vulnerability Management
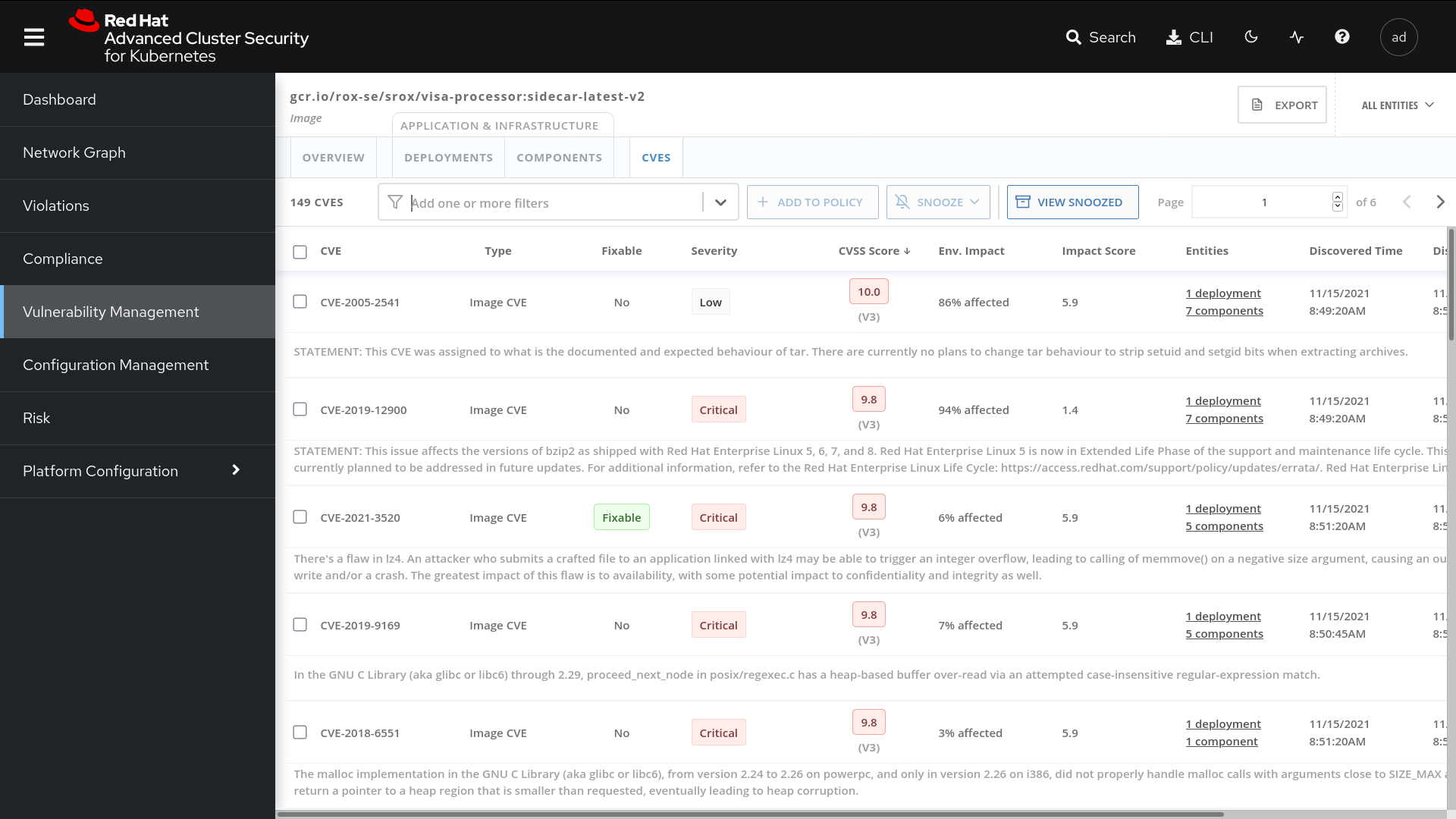
One of the most critical steps in securing containers in OpenShift is to prevent images with known, fixable vulnerabilities from being used as well as to identify and stop running containers that have vulnerabilities. You must also run on-demand vulnerability searches across images, running deployments, and clusters to enforce policies at build, deploy, and runtime.
A vulnerability management solution must also integrate with your CI/CD pipeline to fail a build if it contains a vulnerability while providing the developer details on why the build failed and how to remediate it.
Red Hat Advanced Cluster Security for Kubernetes delivers full life cycle image and container scanning. We combine details about vulnerabilities with Kubernetes data and the life cycle stage that the vulnerability impacts in order to quantify the security risk that a given vulnerability poses to your environment. This also allows us to pinpoint which pods, namespaces, deployments, and clusters are impacted by a given vulnerability.
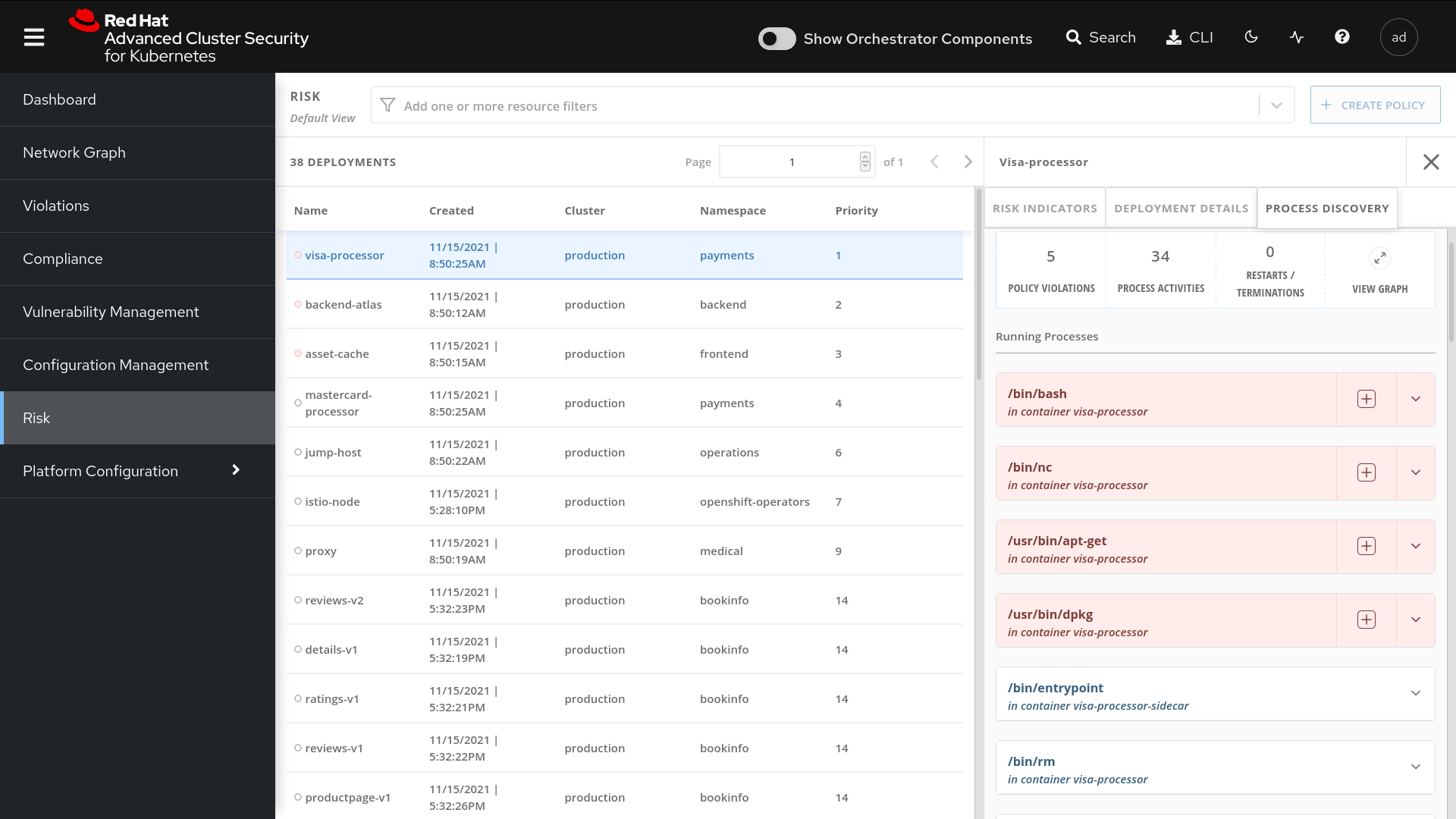
Risk Profiling
A common pain point is being overwhelmed with security alerts and incidents that need investigation without any guidance on prioritization. This approach inevitably leads to instances where high-risk security issues trail low/medium-risk issues in remediation simply because teams cannot identify which problems present the highest risk. Or in the worst case scenario, without prioritization, nothing is remediated.
Red Hat Advanced Cluster Security for Kubernetes provides a numerical risk-based ranking for each deployment based on information across the entire application life cycle. We correlate image vulnerabilities and their severity with rich contextual data that empowers users to understand which deployments are in need of immediate remediation so that the highest risk deployments are addressed first.
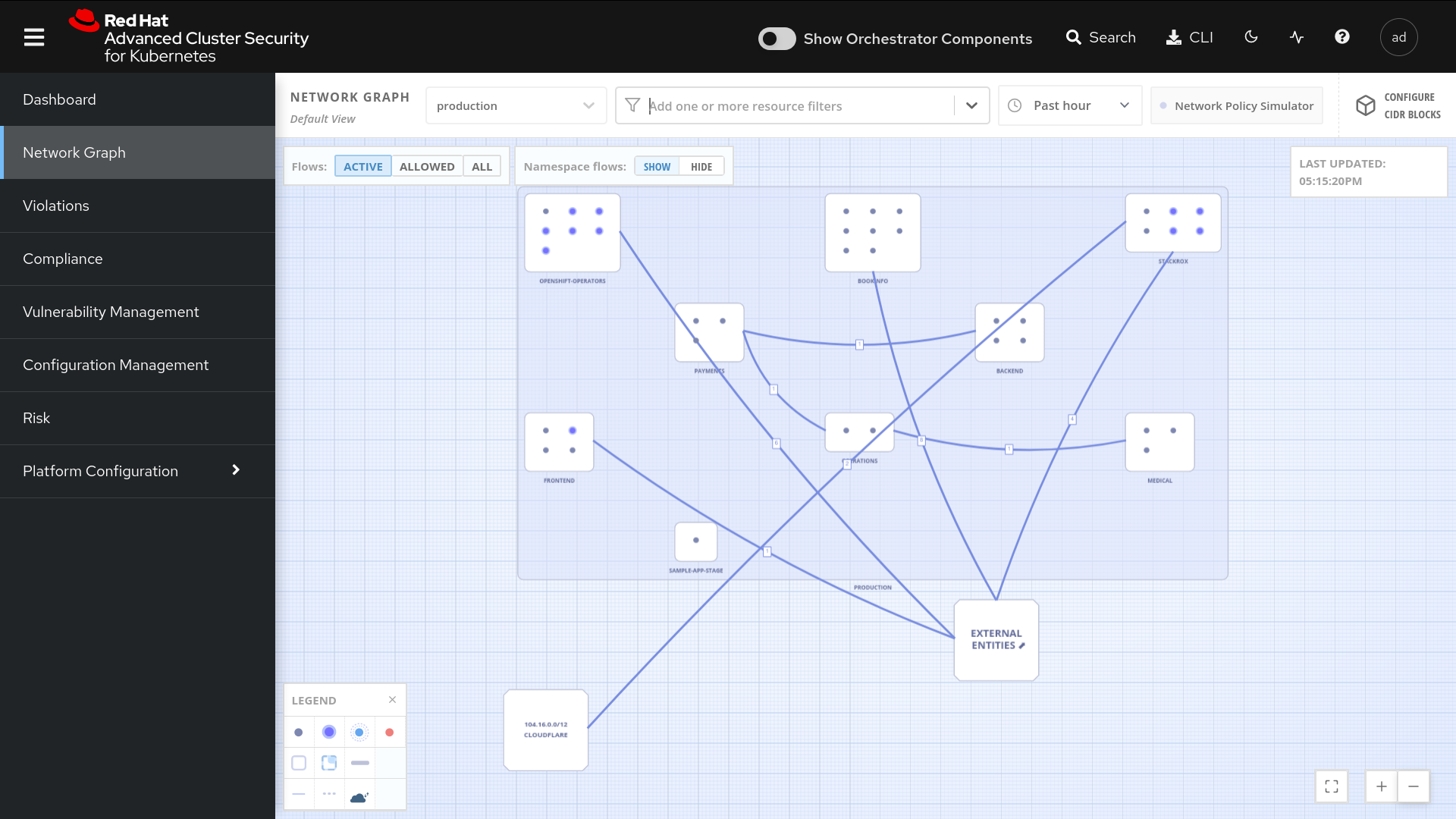
Network Segmentation
Containers pose a unique networking challenge because containers communicate with each other across nodes and clusters (east-west traffic) and with outside endpoints (north-south traffic). As a result, a single container breach has the potential to impact every other container. Therefore, it is imperative to limit a container’s communication in adherence with least privilege principles without inhibiting your container’s functional goals.
Our approach to network segmentation leverages the built-in feature in Kubernetes known as Network Policies, which gives robust and portable enforcement that scales as Kubernetes scales. This also ensures that security, operations, and development teams use a single source of truth and consistent information to effectively restrict network access.
Runtime Threat Detection and Response
Once container images are built and deployed into production, they are exposed to new security challenges and external adversaries. The primary goal of security in the runtime phase is to detect and respond to malicious activity in an automated and scalable way while minimizing false positives and alert fatigue.
Red Hat Advanced Cluster Security for Kubernetes combines automated process discovery and behavioral baselining with automatically creating an allowed list of processes to determine actual threats from benign anomalies.
It also provides pre-configured threat profiles that detect common threats including cryptocurrency mining, privilege escalation, and various other exploits. Because it uses Kubernetes-native controls to mitigate threats with actions such as killing pods and restarting them fresh or scaling deployments to zero, it ensures incident response does not result in application downtime or pose other operational risk.
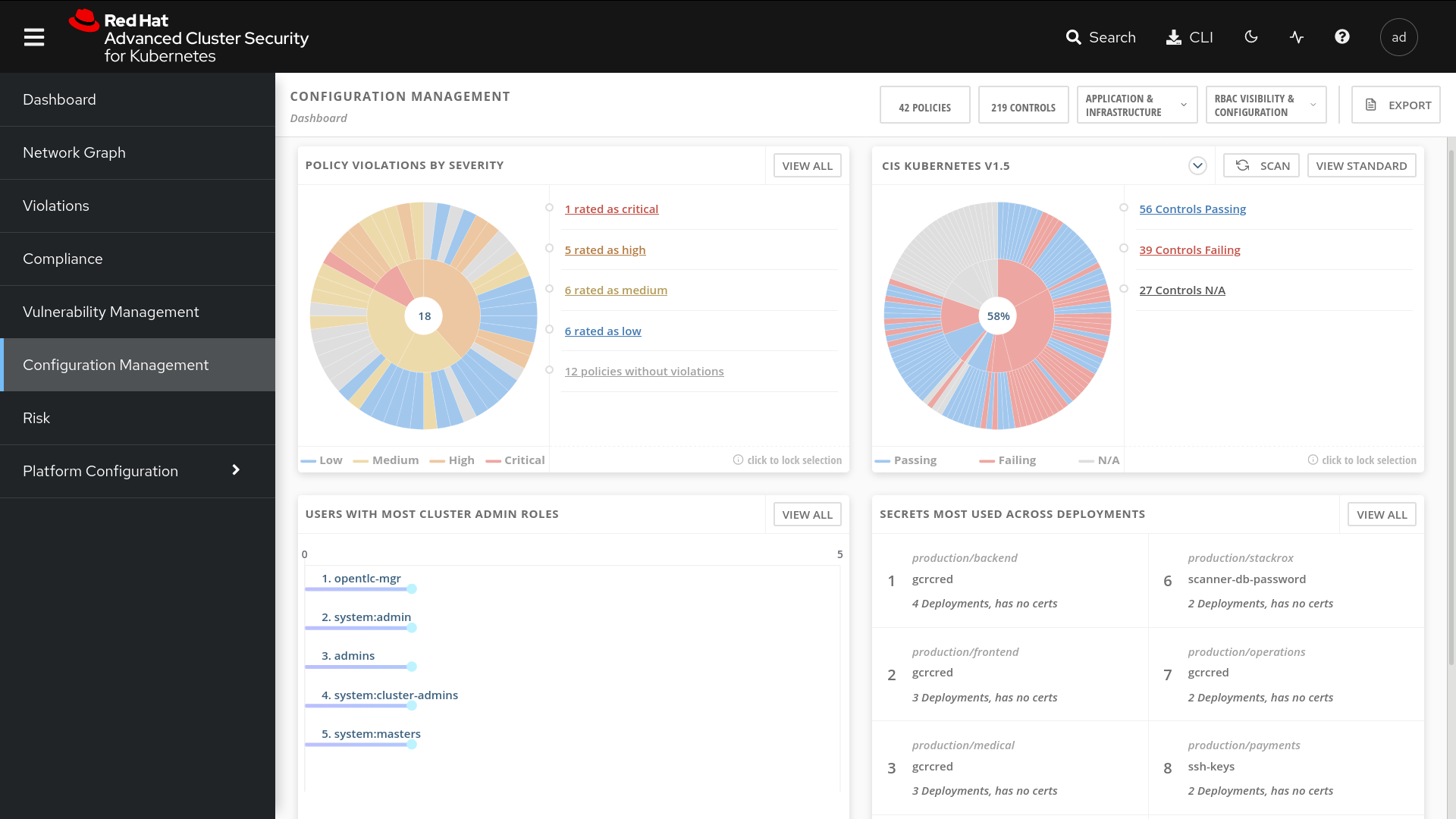
Configuration Management
The configuration options for container and Kubernetes environments run deep and can be challenging for security teams to get right. In sprawling container and Kubernetes environments, it is not advisable to manually check each security configuration for each asset to assess its risk.
While the CIS Benchmarks for Docker and Kubernetes provide helpful guidance and a useful framework for hardening your environment, they contain hundreds of checks for different configuration settings. Ensuring continuous adherence to the CIS benchmarks and other configuration best practices can be challenging without automation.
Red Hat Advanced Cluster Security for Kubernetes gives a deployment-centric view of how their images, containers, and deployments are configured prior to running to identify missed best practices and recommendations. It evaluates how you are using role-based access control (RBAC) to understand user and service account privileges to identify risky configurations. It also tracks the use of secrets to identify unnecessary exposure so you can proactively limit its access.
When it detects misconfigurations, it allows you to build custom policies or use one of its out-of-the-box rules to enforce better configuration – at build time with CI/CD pipeline integration or at deploy time using dynamic admission control.
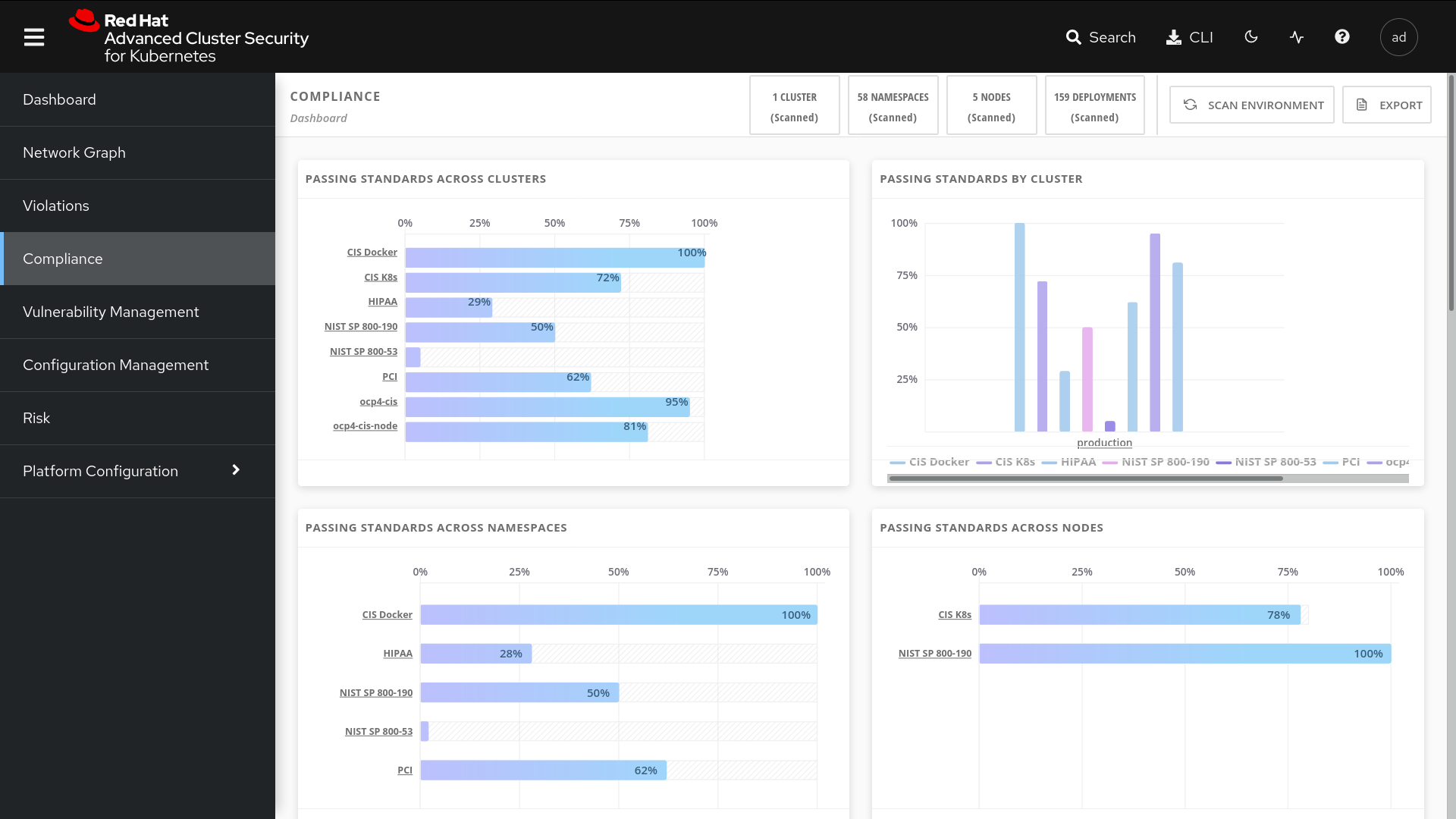
Compliance
DevOps moves fast and relies on automation for continuous improvement; therefore, organizations need a compliance solution built to complement, not inhibit, DevOps activities. You not only need to adhere to industry compliance requirements but also show proof of continuous adherence.
Lastly, you also need to adhere to internal policies for security configurations and other best practices to prevent non-compliant builds or deployments from being pushed to production.
Our Kubernetes-native security solution comes pre-built with compliance checks for CIS benchmarks for Docker, Kubernetes and OpenShift as well as other industry standards such as PCI, HIPAA, and NIST SP 800-90 and SP 800-53. Compliance reports can be generated with a single click and handed to auditors as evidence.
Final Thoughts
Red Hat Advanced Cluster Security for Kubernetes delivers the next generation in container security, with a Kubernetes-native architecture that is both container-native and Kubernetes-native. Leveraging the declarative data and built-in controls of Kubernetes minimizes operational risk, accelerates developer productivity, and reduces operational cost while immediately improving your security posture across applications lifecycle Build, Deploy and Runtime phases. See our recent webinar to learn more about how you can secure your workloads in OpenShift clusters using Red Hat Advanced Cluster Security for Kubernetes.
04:27 PM, Dec 23
Author:

Principal Solutions Architect
Jarosław Stakun
Jaroslaw works as an Principal Solutions Architect at Red Hat and is responsible for delivery and solution selling based on Red Hat Openshift Container Platform and Red Hat Application Services in the region of Central and Eastern Europe.